HIPAA Configuration Auditing
Looking to 2017, there may be new goals, challenges, and projects that face your organization. This is a good time to take the “10,000 foot view” of what your organization wants to address. While this is a great time to outline and plan new projects, this is also an opportune time to reassess current projects, including the controls put in place to address laws and regulations. One of those laws receiving attention in the news recently is the Health Insurance Portability Accountability Act (HIPAA).
Consequences of noncompliance
Passed into law in 1996, HIPAA is certainly not new. HIPAA is an act that addresses administrative, technical, and physical controls around protecting sensitive patient data. Most organizations under HIPAA’s umbrella already have an understanding of what the act means to their organizations in terms of securing sensitive data. But organizations can also grow complacent in their processes and ultimately become noncompliant, as discussed in our Drifting Out of Compliance blog post. This is a dangerous situation for organizations, as the federal government just fined a university $650,000 for being compromised with remote access malware:
“In the 13th major HIPAA enforcement action so far this year (2016), federal regulators have slapped the University of Massachusetts Amherst with a $650,000 financial settlement and corrective action plan after investigating a relatively small 2013 breach involving a malware infection at a campus speech and language center.”
There have been over $12 million HIPAA-related fines in 2016
Information security is a dynamic sector, regularly changing to remain current with trends, and your organization should not overlook controls and processes that act as the foundation of your overall security program. While the HIPAA acronym may be dated in some people’s minds, the enforcement certainly is not. There have already been over $12 million HIPAA-related fines in 2016 alone. Organizations should regularly assess their current processes that pertain to these controls so that they don’t lose track of their effectiveness.
Our blog, Tips for Making The Most of Your Year-End Spending, provides advice on budgeting for the new fiscal year. Two important tips are evaluating your current environment, and identifying the gaps between your current status and goals. Has your environment expanded at all? Does the new environment fall under HIPAA regulation? If so, do you have proper controls in place to protect that environment?
Two important tips: evaluate your current environment, and identify the gaps between your current status and goals
Tenable solutions
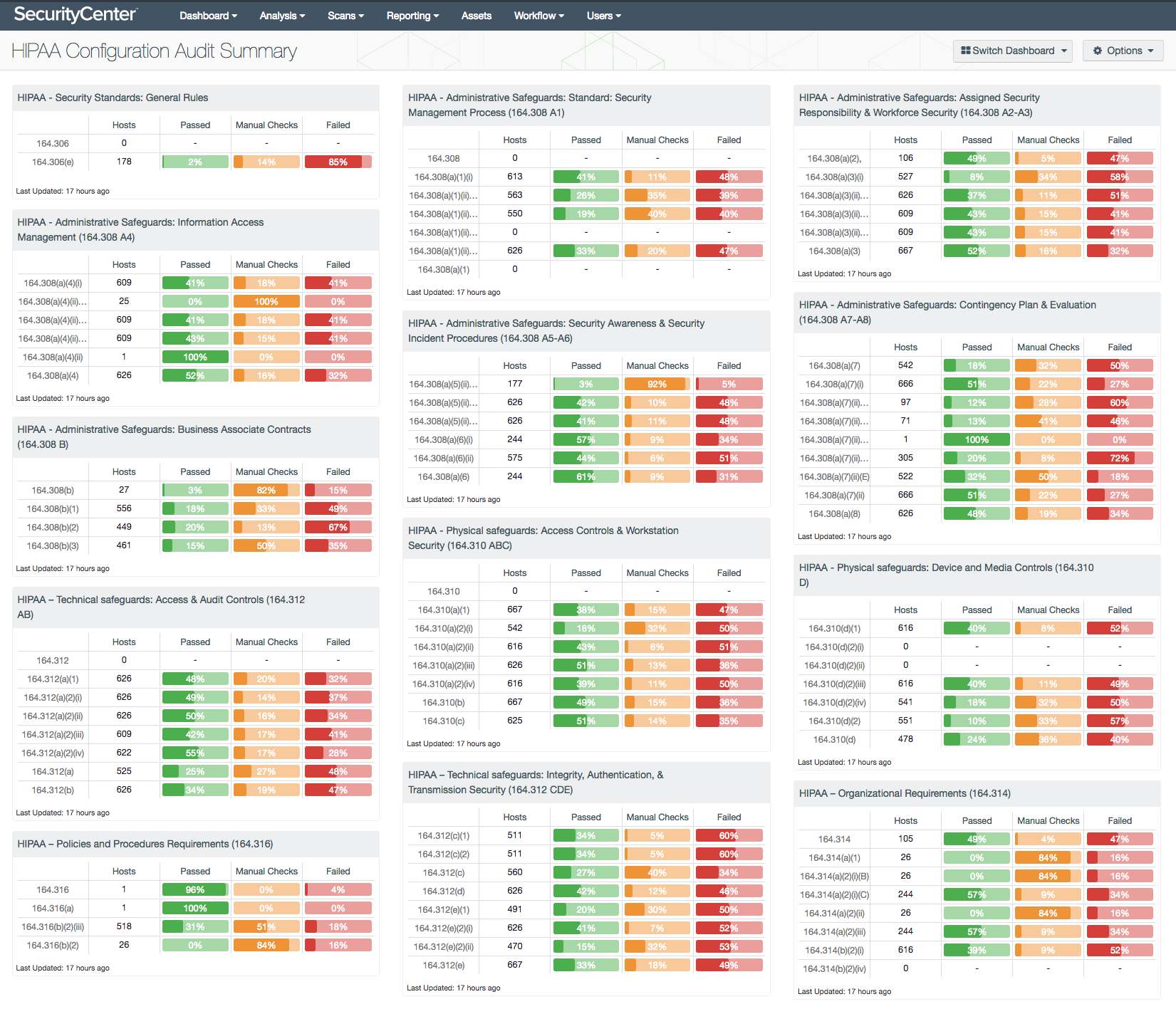
Tenable provides solutions that enable organizations to address these year-end questions by tracking and assessing environments with continuous network monitoring. The Tenable Assurance Report Cards (ARCs) do a great job of quickly analyzing environments against pre-defined baselines with a Pass/Fail grading. Organizations can leverage ARCs to quickly assess whether a previously compliant environment has developed compliance failures, or to grade completely new environments. In addition to ARCs, the HIPAA Configuration Audit Summary dashboard in SecurityCenter Continuous View® (SecurityCenter CV™) has been updated. It provides detailed and relevant data from your environment for security analysis and HIPAA compliance. The dashboard features over ten components that address HIPAA concerns such as:
- Access Control & Workstation Security
- Security Management Process
- Integrity, Authentication & Transmission Security
You can customize these components to fit the uniqueness of your environment. The HIPAA dashboard also automatically tracks the number of hosts for each component, while displaying the percentage of hosts that have passed and the percentage of hosts that have failed.
Conclusion
There are always new trends and concerns to be addressed when securing an environment, but fundamental processes, controls, and compliance should not be forgotten. Organizations can leverage Tenable solutions to keep up with the latest security trends while simultaneously addressing well-established regulation responsibilities such as those put in place by HIPAA.
Related Articles
- Security Frameworks
- Vulnerability Management
- Vulnerability Scanning