by Steve Tilson
June 8, 2017
Organization are constantly being exploited for trade secrets, financial gain or malicious behavior. Attacker techniques are getting harder to detect and intrusions are not always easily identified. Passive monitoring of the data entering and leaving an enterprise network can support a number of forensic objectives, such as discovering the source of security attacks or other problem incidents. Passive network forensics plays an essential role for analyst in combating computer crime for organizations by analyzing abnormal behavior of systems.
Network traffic is transmitted and then lost, unlike stored media, making network forensics more challenging. By looking at the way a given machine interacts with others, we can often determine the role of the machine based solely on the network data. A compromised host behavior can change the way the host acts subtly or in more dramatic ways. These behavioral changes are used to identify role shifts and to trace the malicious or unintentional disperse of that change to other machines.
Information displayed by the components of this dashboard takes a look at that network activity along with event logs that shows possible network intrusion. This dashboard presents information passively detected over the last 72 hours, such as summaries of domains accessed and indicators of suspicious network activity. This information can be helpful for network monitoring and forensics.
The Passive Network Forensics dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring.
The dashboard requirements are:
- SecurityCenter 5.4.5
- Nessus Network Monitor 5.3.0
- LCE 5.0.1
- LCE Client - Tenable NetFlow Monitor
- LCE Client - Tenable Network Monitor
Note that this dashboard relies on PVS detections being forwarded to the LCE. Make sure that the PVS is configured to send syslog messages to the LCE: in Configuration > PVS Settings > Syslog, include the LCE host (with port 514) in the Realtime Syslog Server List. The LCE listens for syslog messages by default.
Listed below are the included components:
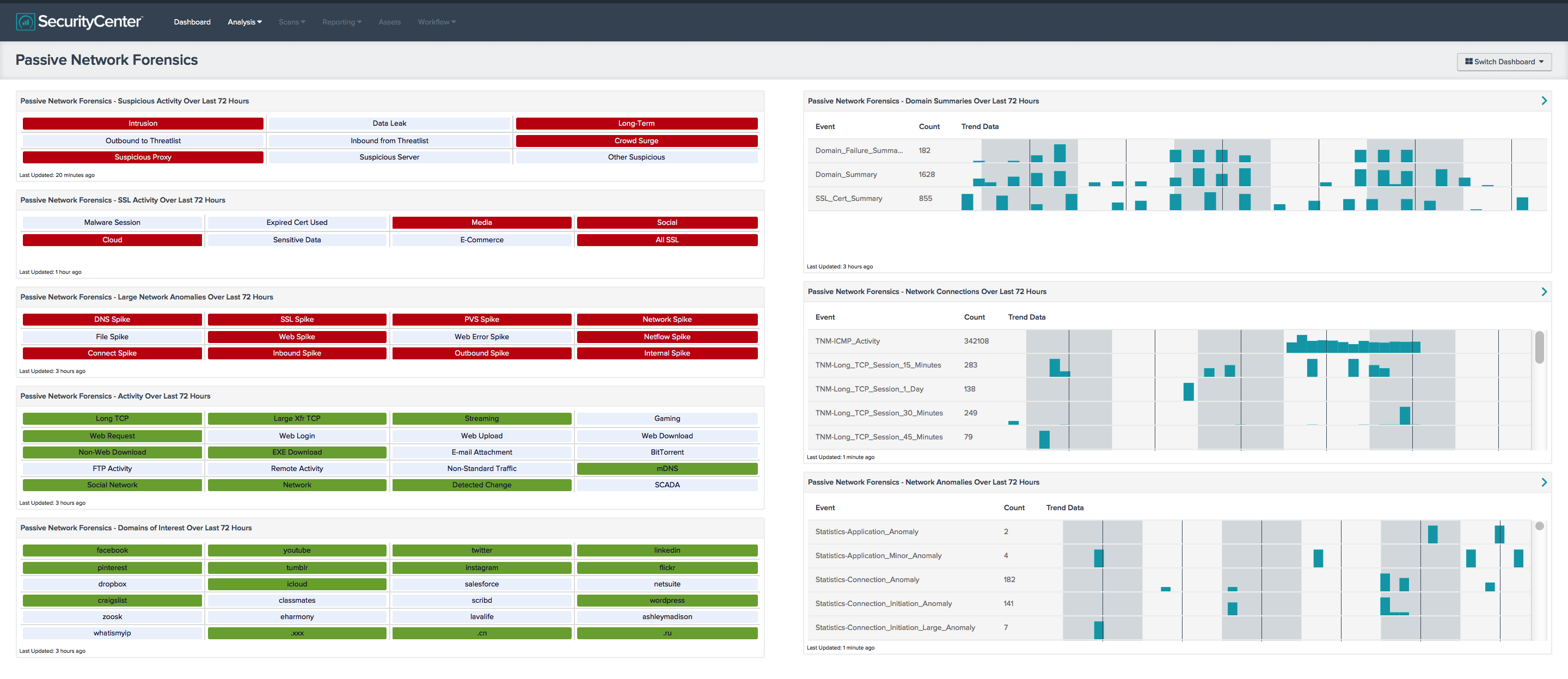
- Passive Network Forensics - Suspicious Activity Over Last 72 Hours - This matrix presents indicators of suspicious events that have occurred in the last 72 hours, including intrusions, potential data leaks, potentially unwanted long-term activity, threatlist activity (interaction with known botnets), crowd surges, suspicious proxy activity, suspicious server activity, and other suspicious host activity.
- Passive Network Forensics - SSL Activity Over Last 72 Hours - This matrix presents indicators of SSL events that have occurred in the last 72 hours, including use of SSL certificates known to be associated with malware, use of expired SSL certificates, media access (such as Netflix or Skype), social media access (such as Facebook or Twitter), cloud file storage access, access to services commonly used for sensitive data, and access to services used for processing credit card transactions. The last indicator notes all passively detected SSL activity; this includes the above, plus other activity that might be of interest.
- Passive Network Forensics - Large Network Anomalies Over Last 72 Hours - This matrix presents indicators of large network anomalies that have occurred in the last 72 hours, including spikes in DNS events, SSL events, PVS events, network events, file access events, web access events, web error events, NetFlow events, and connection events (including inbound, outbound, and internal). Event rates are compared by hour to the same hour in previous days; large spikes in event rates can indicate new applications, new types of network usage, and in some cases, abuse.
- Passive Network Forensics - Activity Over Last 72 Hours - This matrix presents indicators of network activity that has occurred in the last 72 hours, including long TCP sessions (more than 47 hours), TCP sessions with large data transfers (1GB or more), streaming traffic (such as Netflix or XM Radio), gaming traffic (such as logins to gaming networks), web activity (requests, logins, uploads, and downloads), non-web downloads, EXE downloads, e-mail attachment detections, BitTorrent activity, FTP activity, remote activity (SSH, VNC, or RDP), non-standard traffic (such as non-HTTP traffic on port 80), mDNS traffic, and SCADA traffic. Indicators are also presented for activity that falls under the event types of social network activity, general network activity, and detected changes.
- Passive Network Forensics - Domains of Interest Over Last 72 Hours - This matrix presents indicators of domains of interest accessed over the last 72 hours. This component can be altered to add or remove domains of interest as needed. The Domain_Summary, Domain_Failure_Summary, and SSL_Cert_Summary events all give lists of domains accessed; searches are done within these events to find specific domains of interest. Each summary event for a given IP address gives the domains accessed by that IP since the last such event for that IP (which may be as often as hourly).
- Passive Network Forensics - Domain Summaries Over Last 72 Hours - This table presents summary events for domains accessed over the last 72 hours, with trending. The Domain_Summary, Domain_Failure_Summary, and SSL_Cert_Summary events all give lists of domains accessed; searches can be done within these events to find specific domains of interest. Each summary event for a given IP address gives the domains accessed by that IP since the last such event for that IP (which may be as often as hourly).
- Passive Network Forensics - Network Connections Over Last 72 Hours - This table presents network connection events from the Tenable Network Monitor (TNM) that have occurred over the last 72 hours, with trending. These events record network sessions, and indicate length and amount of data transferred. Note that a long TCP session maybe recorded twice – once for the length and once for the amount of data transferred.
- Passive Network Forensics - Network Anomalies Over Last 72 Hours - This matrix presents indicators of network anomalies that have occurred in the last 72 hours. Minor, medium, and large anomalies are tracked for each event type. Event rates are compared by hour to the same hour in previous days; spikes in event rates can indicate new applications, new types of network usage, and in some cases, abuse.