by Cody Dumont
April 6, 2016
Governance, Risk Management, and Compliance (GRC) is a substantial part of any information assurance program. A GRC requires information systems to be audited, regardless of the standard to which the audit is performed. This dashboard provides the audit results for Mac OS X operating systems.
One of the initial steps in a successful GRC program is to set configuration guidelines and establish a supportable set of security policies. Tenable.sc Continuous View (CV) can measure compliance using audit files that cover a wide range of major regulations and other auditable standards. Tenable provides over 500 audit files, which are available for download from the Tenable Support Portal, in categories such as operating systems, applications, databases, and network devices. Tenable products can be used to audit systems based on SCAP content, and many Tenable audit policies have been certified by the Center for Internet Security (CIS). More information about audit files can be found in the Tenable Discussion Forums, Tenable Support Portal, Nessus Compliance Checks, and Nessus Compliance Reference.
Tenable.sc (CV) using Nessus has several built-in functions to perform the Mac OS X compliance checks. Mac OS X compliance checks can be conducted on XML files, by executing commands from the command line, and several other methods. There are also built-in checks such as password length, permission management, and Suspicious File Content. Other more complex checks can use regular expressions and other pattern matching methods.
Audit files can be customized to match the values defined by an organization's corporate policies. Audit files are easily created or modified to support the organization’s existing security policies. When an audit scan is performed, for each individual compliance check, Nessus attempts to determine if the host is compliant, non-compliant, or if the results are inconclusive and need to be verified manually. Unlike a vulnerability check that only reports if the vulnerability is actually present, a compliance check always reports a result. The data collected can be used as the basis of an audit report to show that a host passed or failed a specific test, or if configuration check could not be properly tested.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments. The dashboard requirements are:
- Tenable.sc 5.1.0
- Nessus 8.5.2
- Compliance Data
- This dashboard requires “Full Text Search” to be enabled for each analyzed repository.
Tenable.sc CV is the market leader in providing a unique combination of vulnerability detection, compliance auditing, and reporting. Tenable.sc CV supports auditing more technologies than any other vendor, including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. This makes Tenable.sc CV the market-defining continuous network monitoring platform, and Nessus the market-defining vulnerability scanning for auditors and security analysts.
Components
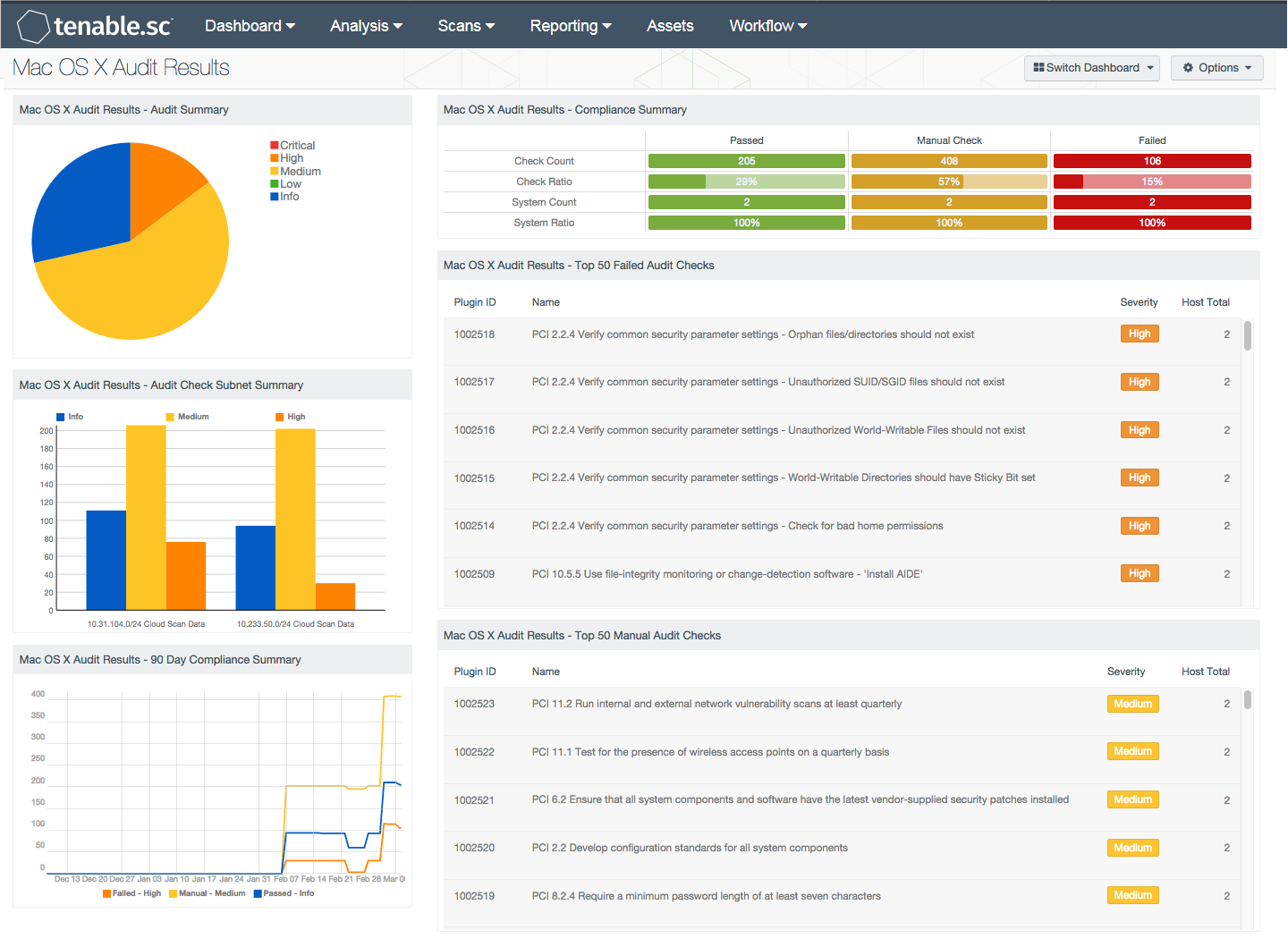
Mac OS X Audit Results - Audit Summary: The Mac OS X Audit Summary is a severity-based pie chart that helps to summarize the current compliance status. The chart provides a conceptual view of the compliance status. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Informational severity status is used for checks that have passed the compliance check.
Mac OS X Audit Results - Audit Check Subnet Summary: The Mac OS X Audit Check Subnet Summary chart provides a summary of the top 30 affected subnets. The columns are sorted using the failed compliance check (vulnerability) count column.
Mac OS X Audit Results - 90 Day Compliance Summary: The Mac OS X 90-Day Compliance Summary line chart provides analysts with a historic view of compliance status over the past 90 days. There are three lines on the graph: one each for passed checks, manual checks, and failed checks. The values calculated at each data point provide a count of checks over the previous 3 days, which provides a more accurate view of the change in data.
Mac OS X Audit Results - Compliance Summary: The Mac OS X Compliance Summary matrix provides a high-level view of the Mac OS X compliance status. The first two rows provide the total count of Passed checks, Failed checks, and checks requiring a manual review. The first row, 'Check Count', provides a count of the current checks per check status. The second row, 'Check Ratio', provides a ratio view of check status. The three columns together should total 100%. The last two rows provide a system count analysis. The third row, 'System Count', provides the number of systems with at least one audit check in the applicable state. The last row, 'System Ratio', provides a percentage of systems with at least one audit check in the applicable state. The matrix is composed of three colors. Red is for checks that have failed to meet the compliance threshold. Orange is for checks that need to be manually reviewed to assess their compliance state. Green is for checks that have passed the compliance check.
Mac OS X Audit Results - Top 50 Failed Audit Checks: The Mac OS X Top 50 Failed Audit Host Details table is an informative table providing the most common audit checks that have failed the compliance check. Audit checks that have failed the compliance check are out of the compliance range. For example, if the audit check is for password length and the expected range is 8 - 15 characters, and policy is set to 16 - 25, the check would fail even though the policy is more strict than the audit check. The table provides the audit check name, severity, and total hosts affected. The table is sorted using the 'Host Total' column.
Mac OS X Audit Results - Top 50 Manual Audit Checks: The Mac OS X Top 50 Manual Audit Host Details table is an informative table providing the most common audit checks that need to be manually verified. The table provides the audit check name, severity, and total hosts affected. The table is sorted using the 'Host Total' column.