by Josef Weiss
July 23, 2014
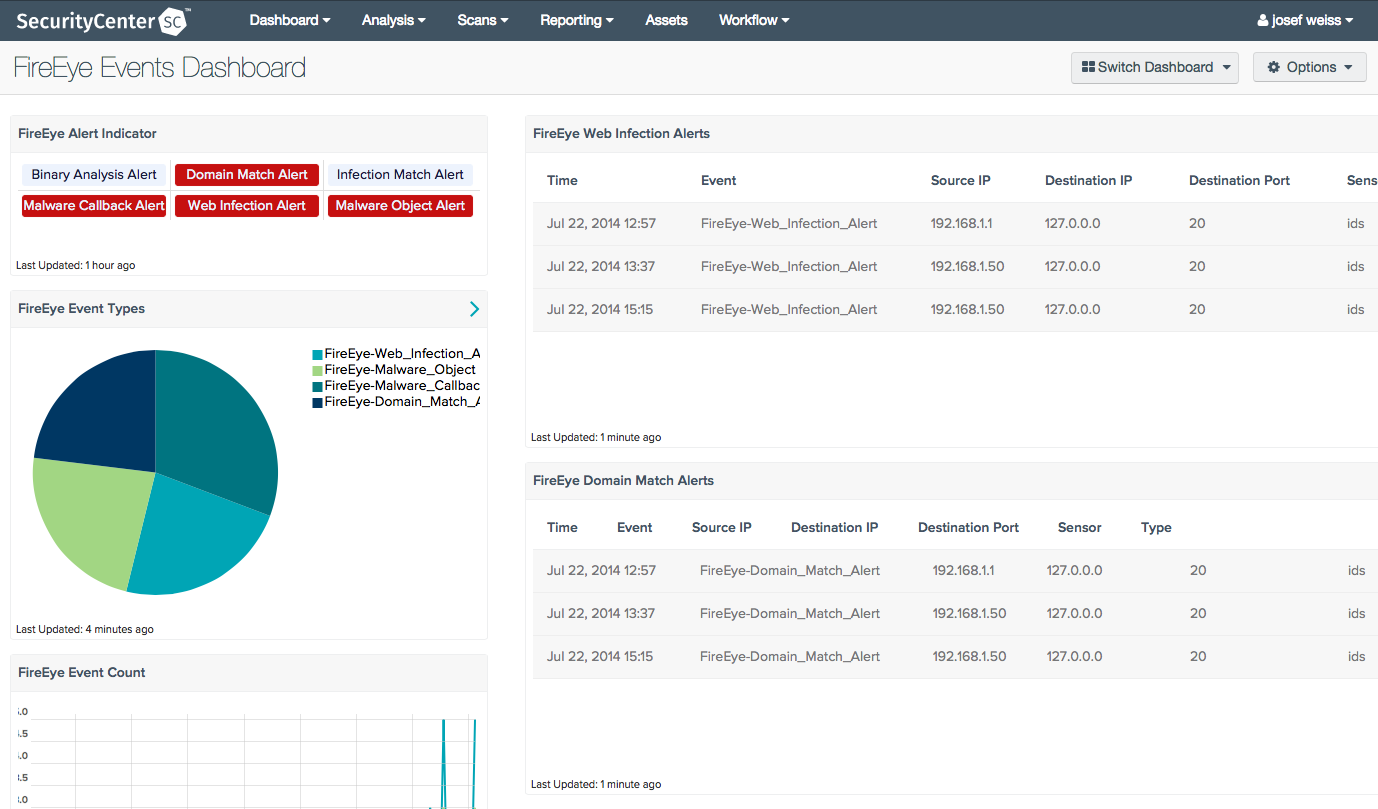
When managing an organization’s risk, being able to evaluate security events is an important first stage. Understanding potential indicators of compromise allows organizations to better manage evolving threats. The FireEye Events Dashboard displays a summary status of FireEye events, providing an overview of collected events using several techniques. This dashboard further allows organizations to consolidate event data from multiple devices into one location, without the need for individual access.
Organizations have the responsibility to translate a mountain of security data to understand the security risk imposed on them. This dashboard displays events collected from a FireEye device and includes indicators based on triggered FireEye events. Organizations that utilize FireEye platforms to protect themselves against advanced cyber threats will benefit from this dashboard.
Using FireEye audit checks, this report highlights the pass/fail results of audit checks, allowing a security analyst to review the configuration and status of the device without requiring device management privileges. This information provides risk managers and system administrators with a list of items which require immediate focus and provides leadership with easy to understand pass/fail audit findings.
With this information, security teams and system administrators can better understand possible gaps in threat prevention which require additional focus. When using this dashboard, the security team can easily identify and focus on specific problem areas and triggered events that require further investigation. System administrators can take the same information to help set the priority to corrective actions and mitigation strategies. Overall this dashboard is beneficial to several groups within the organization to better reduce cyber risk.
The dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The report can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 4.8.2
- LCE 5.0.2
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. SecurityCenter Continuous View® (SecurityCenter CV™) offers organizations a unique peace of mind by identifying their biggest threats and enable them to respond quickly. SecurityCenter CV™ provides a unique combination of detection, reporting, and pattern recognition utilizing industry recognized algorithms and models. SecurityCenter CV™ combines active scanning, log analysis, and deep packet inspection to continuously discover and track users, applications, cloud infrastructure, trust relationships, and vulnerabilities.
Components
FireEye Alert Indicator - This indicator component highlights on triggered events that have been forwarded to the LCE by a FireEye appliance. Incoming event data is matched to a Normalized Event Type and illuminated red to indicate that an alert has been received within the last 72 hours.
FireEye Event Types- This pie chart presents a breakdown of triggered FireEye event types, relative to the overall total of currently existing FireEye events over the last 7 days.
FireEye Event Count - This component displays a 7 day trend of the total number of FireEye triggered events along with malware events. This allows the analyst to view spikes in FireEye alerts over the past week, and to correlate malware specific events against the total event count.
FireEye Event Analysis - This component displays a trend data of FireEye events, the associated counts of those events, and the name of the triggered event over the last 72 hours. This is presented via a Normalized Event Summary on the FireEye event type.
FireEye Web Infection Alerts - This table presents the analyst with a detailed listing of the last 7 days of FireEye Web Infection alerts. Displayed within the table are the time the event occurred, event name, source IP address, destination IP address, destination port, the reporting sensor, and the event type category, which is filtered on in this particular FireEye alert. The reporting period is 7 days.
FireEye Domain Match Alerts - This table presents the analyst with a detailed listing of the last 7 days of FireEye Domain Match alerts. Displayed within the table are the time the event occurred, event name, source IP address, destination IP address, destination port, the reporting sensor, and the event type category, which is filtered on this particular FireEye alert. The reporting period is 7 days.
FireEye Malware Callback Alerts - This table presents the analyst with a detailed listing of the last 7 days of FireEye Malware Callback alerts. Displayed within the table are the time the event occurred, event name, source IP address, destination IP address, destination port, the reporting sensor, and the event type category, which is filtered on this particular FireEye alert. The reporting period is 7 days.
FireEye Malware Object Alerts - This table presents the analyst with a detailed listing of the last 7 days of FireEye Malware Object alerts. Displayed within the table are the time the event occurred, event name, source IP address, destination IP address, destination port, the reporting sensor, and the event type category, which is filtered on this particular FireEye alert. The reporting period is 7 days.