by Stephanie Dunn
May 5, 2016
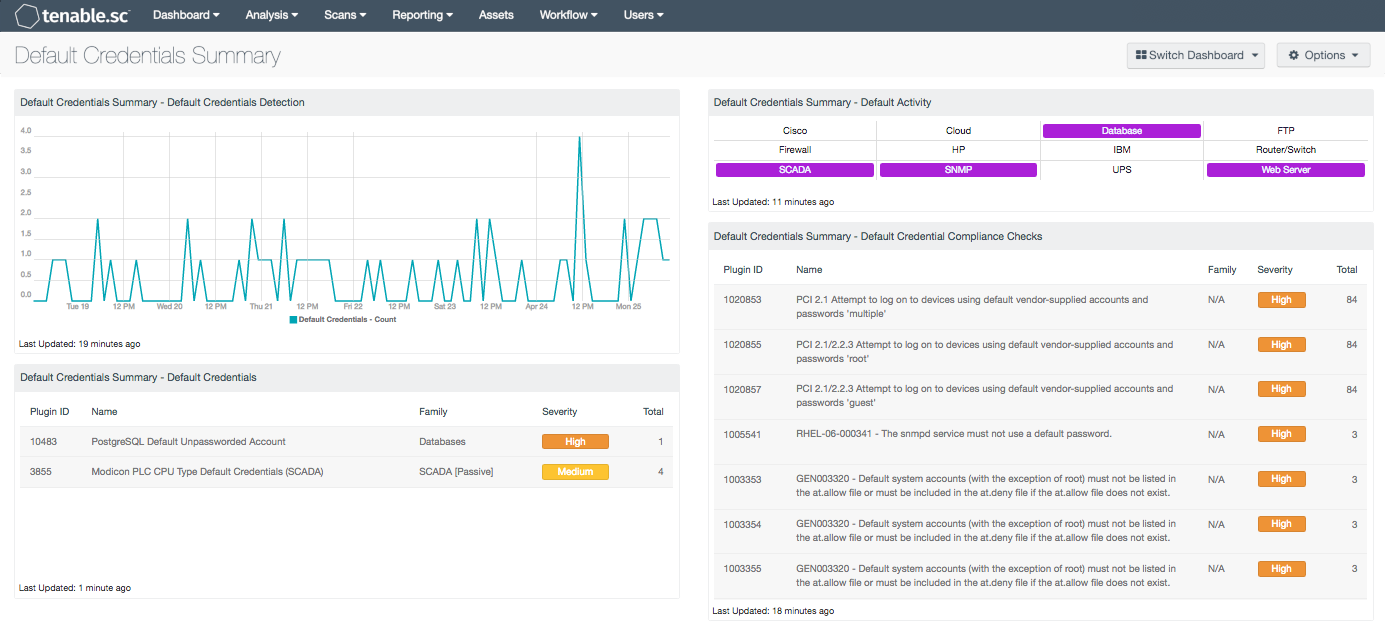
Within the past few years, many organizations have placed greater focus on securing network devices, services, and applications due to the increase in security threats. Many devices and services include well-known default credentials that are not changed or properly secured, and that are frequently exploited by attackers to gain access to a network. This dashboard presents a comprehensive summary of systems with default accounts, passwords, and credentials that have been detected on a network.
As devices and services are deployed on a network, many administrators fail to rename, change, or properly configure default usernames, passwords, and credentials. Some of these devices and services can include routers, web applications, databases, and network protocols. SCADA devices are notorious for having default vendor-supplied credentials. Most operating systems also include default account names or credentials that are not changed before being placed into production environment. Default accounts can consist of vendor-supplied usernames and/or password credentials. Accounts with default credentials can be overlooked by administrators, and may result in administrators failing to disable or delete the default account or changing default passwords to a weak or non-complex password. Additionally, some administrators may also be unaware of user accounts with default credentials. If possible, organizations should replace default accounts with unique usernames. Along with changing default credentials, implementing security controls such as account lockouts and password complexity can help reduce the risk of account exploitation.
This dashboard can assist organizations by quickly identifying systems utilizing default accounts and credentials on the network. Using Nessus and NNM, organizations can obtain real-time information on devices and services using accounts with default credentials. Leaving default credentials in place can be disastrous for an organization, as many default credentials are well known by attackers and can be easily guessed or brute-forced. Compliance checks for default account names, passwords, and credentials will alert analysts to systems that could be potentially at risk for attack. Many regulatory compliance controls, including the Payment Card Industry Data Security Standard (PCI DSS) Version 3.1 prohibits the use of vendor-supplied default passwords. The Center for Internet Security Critical Security Controls (CIS CSC) recommends changing default passwords on all applications, operating systems, devices, and critical systems within an organization. Securing accounts on critical devices and services is an essential step for an organization to maintain and strengthening security as well as maintain overall compliance.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The dashboard requirements are:
- Tenable.sc 5.3.1
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
- Compliance Data
- Local Checks
Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc CV is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. NNM provides deep packet inspection to continuously discover vulnerabilities on devices and systems. By integrating with Nessus and NNM, Tenable.sc CV’s continuous network monitoring is able to detect events and vulnerabilities across the enterprise.
The following components are included in this dashboard:
- Default Credentials Summary - Default Credentials Detection: This chart presents the trend of default credential detections on the network within the past seven days. Trend line events are triggered by a NNM plugin that detects default credentials. Information in this chart can be useful for analysts in detecting systems utilizing default usernames, passwords, and credentials.
- Default Credentials Summary – Default Credentials: The Default Credentials table presents hosts with default account names, default passwords, or default credentials in use. Many devices, operating systems, web applications, and services include vendor-supplied default credentials. This component leverages Nessus and NNM to obtain real-time information on accounts using default credentials. Analysts and security teams will find the information provided in this table beneficial in ensuring that systems are not deployed with default credentials.
- Default Credentials Summary – Default Activity: The Default Activity Matrix presents a list of devices, services, and applications utilizing default credentials. Ideally devices, services, and applications on a network should not have any default usernames, passwords, or credentials in use. If the vulnerability is detected, the indicator will change color to purple. Clicking on a highlighted indicator will bring up the analysis screen, where more detailed information such as IP addresses, possible solutions, and additional information on affected systems can be obtained. This component can be modified to include specific or additional plugins that detect default credentials.
- Default Credentials Summary – Default Credential Compliance Checks: The Default Credential Compliance Checks table presents a list of audit checks performed to detect default usernames, passwords, and credentials on a network. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Compliance failures in this table can be the result of services using default credentials, devices with vendor-supplied passwords, default operating system accounts, and more. Organizations should review current security policies and compliance requirements that are relevant to the organization.