by Cody Dumont
December 13, 2016
To protect the citizens of Canada, the Canadian Government has analyzed trends in cyber threat activity that impacts government Internet-connected networks. The result of the study is Information Technology Security Bulletin 89 revision 3 (ITSB-89 rev.3), “Top 10 IT Security Actions to Protect Government of Canada Internet-Connected Networks and Information”. The Canadian Government provides a series of guidelines and bulletins to assist government offices and private businesses in securing their information systems. This dashboard provides executive level content that demonstrates how Tenable.sc Continuous View (CV) can help Canadian organizations comply with regulations and best practices.
The Top 10 Actions are:
- Use Shared Services Canada (SSC) Internet gateways
- Patch operating systems (OSs) and applications
- Enforce the management of administrative privileges
- Harden Operating Systems (OSs)
- Segment and separate information
- Provide tailored awareness and training
- Manage devices at the enterprise level
- Apply protection at the host level
- Isolate web-facing applications
- Implement application whitelisting
While Tenable products cannot directly address each of these actions, the data collected by Tenable.sc CV can help Canadian Government agencies in addressing each of these actions. For actions that Tenable can only assist with, such as 1, 5, and 6, Tenable.sc CV can provide context and a deeper understanding. For Action 6, for example, the security operations team can easily use the vulnerability summary views or other dashboards to illustrate current security threats. Agencies that use Tenable’s Log Correlation Engine (LCE) and Nessus Network Monitor (NNM) can monitor network flows and easily identify suspicious traffic patterns, which can help with Actions 1 and 5. This dashboard provides a sampling of many different types of data collected as part of active vulnerability scanning and passive listening.
For the other seven actions defined in ITSB-89 rev.3, Actions 2, 3, 4, 7, 8, 9, and 10, agencies can use this dashboard to easily see how they measure up. These remaining seven actions include patching strategies, privilege enforcement, system hardening (ITSG-33), managing devices, host level protections, web application security, and application white listing. The components in this dashboard provide analysts with several examples of how to analyze the vulnerability data to support each of the actions. In addition, the Tenable.sc feed has a plethora of templates that agencies can use to monitor for compliance with the Top 10 Actions.
Action 4 (Harden Operating Systems) is one of the more complicated actions and is supported by Tenable.sc CV. The action specially calls out Information Technology Security Guidance Publication 33 (ITSG-33) for guidance on system hardening. The ITSG-33 guidance specifies standards for critical security areas such vulnerability management and how agencies can effectively tackle the threat from all vulnerabilities. The Communications Security Establishment Canada (CSEC) developed a series of guidelines for security practitioners in managing information technology (IT) security risks for Government of Canada (GC) information systems. The ITSG-33, IT Security Risk Management: A Lifecycle Approach, provides a comprehensive set of security controls that are used to support a wide variety of business requirements.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive. The dashboard requirements are:
- Tenable.sc 5.4.1
- Nessus 8.5.1
- NNM 5.9.1
- LCE 6.0.0
- Compliance Data
Tenable's Tenable.sc CV helps to identify an agency's vulnerabilities and eliminate blind spots. By detecting missing patches, incorrect configurations, lapsed defenses, incomplete monitoring, and network intruders, Tenable.sc will be able to assist in the mitigation process and monitor for future resurgence. Tenable.sc CV enables agencies to identify risk across the entire network. With more supported technologies than other vendors, Tenable.sc CV is able to analyze vulnerabilities and collected logs from a wide range of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure devices. Tenable.sc's proven approach to continuous monitoring identifies the biggest risks across the agency, and provides the security operations team with the ability to react to advanced threats, zero-day vulnerabilities, and new forms of regulatory compliance.
Components
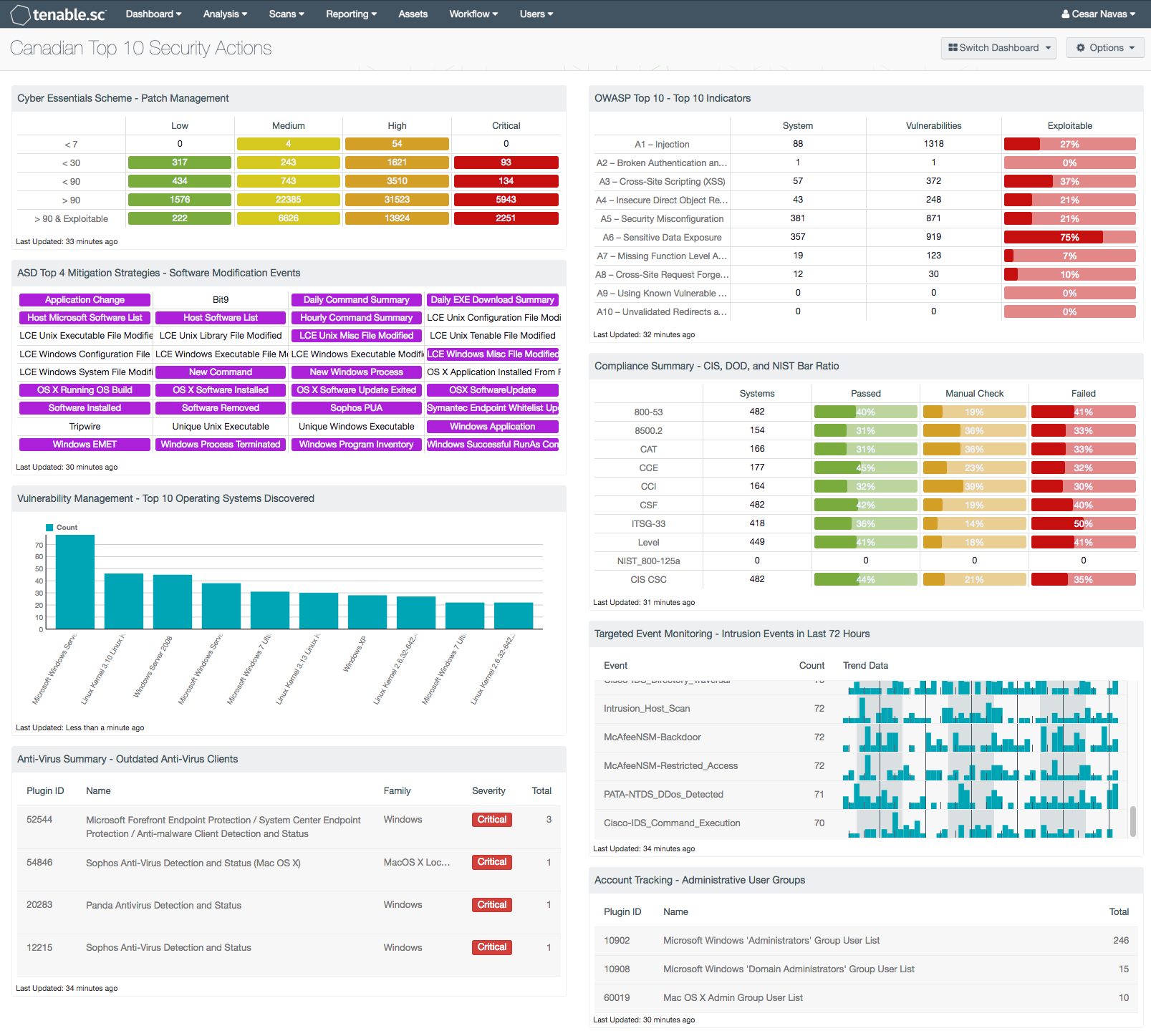
Cyber Essentials Scheme - Patch Management: This component assists with the Cyber Essentials Scheme, Patch Management requirement. The component provides a summary of vulnerabilities and patch release dates. The dates are summarized with 7, 30, 90, more than 90 days and more than 90 days and exploitable. The matrix provides columns for each severity, ranging from low to critical. The low severities are displayed with a green background and white text, and the medium severities are white on yellow. The high and critical severities are orange and red with white text. The results are useful because as stated by the Verizon DBIR 2015 Report, 99.9% of exploited systems had missing patches that were both actively exploitable, and over one year old.
ASD Top 4 Mitigation Strategies - Software Modification Events: This component provides an indicator for file changes or modification events collected from systems with LCE Clients installed, or from systems where syslogs are collected. For each indicator, when a pattern match is found, the indicator will turn purple. Some of the event indicators in the matrix are application changes, a Windows executable file has changed, and UNIX library file changes. The indicators of this component provide system administrators with a central location to monitor for authorized or unauthorized software execution, installation, or changes. Regardless of if the software is downloaded from the internet or a USB drive, LCE Client software can log the application events. When configured appropriately, whitelisting can help prevent unauthorized intruders from modifying or adding software to secure servers or workstations.
Vulnerability Management - Top 10 Operating Systems Discovered: This component provides a summary of the top 10 most discovered operating systems. Using the List OS tool, the bar chart will display the top 10 most common operating systems. Some organizations might consider changing the sort order and looking for the least used operating systems. By identifying the least used operating systems, the analysts can identify the outliers and look for systems possibly not authorized on the network. In either use case, this component will provide a quick and easy to understand view of operating systems on the network.
Anti-Virus Summary - Outdated Anti-Virus Clients: This component assists organizations in monitoring the network for outdated anti-virus clients. Information provided within this component may indicate systems with anti-virus clients that are offline, disconnected, or out-of-date. Analysts can use the information provided to ensure that all anti-virus clients remain connected and up-to-date.
OWASP Top 10 - Top 10 Indicators: This component collects the vulnerabilities from the CGI Abuses, CGI Abuses : XSS, and Web Servers plugin families for both active and passive vulnerabilities. The CGI Abuses family Checks for web-based CGI programs with publicly documented vulnerabilities. These checks include SQL injection, Local File Inclusion (LFI), Remote File Inclusion (RFI), Directory Traversal, and more. For web-based CGI programs with publicly documented cross-site scripting (XSS) vulnerabilities, the CGI Abuses : XSS plugin family is used. For web server vulnerabilities, the Web Server plugin family can detect vulnerabilities in web servers such as Apache HTTP Server, IBM Lotus Domino, Microsoft IIS, and many more.
Compliance Summary - CIS, DOD, and NIST Bar Ratio: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are: NIST, DoD, CCE, CCI, CSF, and CSC. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
Targeted Event Monitoring - Intrusion Events in Last 72 Hours: This table displays the intrusion events by count detected in the last three days. Events are normalized by LCE and filtered on the event type “intrusion,” which denotes logs from network IDS, firewalls, applications, and operating systems that indicate some sort of network attack. This component alerts analysts to recent potential intrusion attempts to allow for remediation or reconfiguration.
Account Tracking - Administrative User Groups: Administrative users typically have unrestricted access to internal systems; tracking administrative users and groups is essential for ensuring the security of network assets and data. This component presents administrative groups that have been detected on the network. This information is obtained through Nessus credentialed scans. These detections will contain lists of administrative accounts in their output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including the output. Security teams can use this detailed information to both track administrative users and detect any users who may have excessive privileges.