by Cody Dumont
April 4, 2017
Cyber security is becoming a primary concern for all nations, including the Republic of China. The impact of losing the ability to process consumer transactions for merely an hour could be devastating to the economy. Cyber security issues cannot be resolved by a single product or technology. To address the vulnerabilities within cyber security, a good baseline of assets must be identified. Usable technology must be deployed and enforceable procedures implemented. This dashboard helps members of the Bankers Association of the Republic of China to gauge their progress in mitigating cyber threats.
The Internet is a daily necessity and is used in many ways such as accessing social media, reading news, and paying bills, just to name a few. How would the organization be impacted if the network were down for a full day?
The Bankers Association of the Republic of China (BA-RoC) published a document called “Information System Security Benchmark and Usage” for financial institutions. The benchmark provides detailed descriptions of the best practices financial institutions should adhere to and model their security operations on. The document provides guidance on several key areas such as information security policy, management scope, implementation, operation, monitoring, and improvement. Listed below are several of the Techniques outlined by the Benchmark supported by Tenable.sc Continuous View (CV):
- Technique 18 - Strengthen system loading monitoring
- Technique 26 - Deploy Password Security Policy
- Technique 27 - Should identify and verify remote devices
- Technique 28 - Should have mechanism to prevent data loss on storage
- Technique 29 - Should be able to prevent data loss during transmit
- Technique 31 - Should deploy file access control to important files
- Technique 42-1 - Control unnecessary and unauthorized access to email or web
- Technique 44 - Maintain minimum amount of devices that can access from external networks
- Technique 45 - Monitor unauthorized access
- Technique 49 - Should have defense mechanism for computer viruses and malware
- Technique 50 - Should able to detect computer viruses and malware
- Technique 51 - Should have action plan when computer virus or malware infection found
The Benchmark highlights the importance of defining security baselines and includes the requirements for the baselines and several implementation examples. The baseline section covers different areas including device, operational, and technical example requirements. The dashboard provides organizations with an overall view of their security posture and helps to identify significant risks. The components map to the different techniques mentioned in the benchmark, which will assist analysts and ensure the implementation of an effective cyber security and risk management program.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.2
- Nessus 8.5.1
- LCE 6.0.0
- Compliance Data
Tenable's Tenable.sc Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities and new types of regulatory compliance configuration audits. Tenable Nessus Network Monitor (NNM) performs deep packet inspection to enable discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure. Tenable Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track systems, applications, cloud infrastructure, trust relationships, and vulnerabilities. By integrating with Nessus, NNM, and LCE, Tenable.sc CV’s continuous network monitoring is able to detect systems and vulnerabilities across the enterprise.
Components
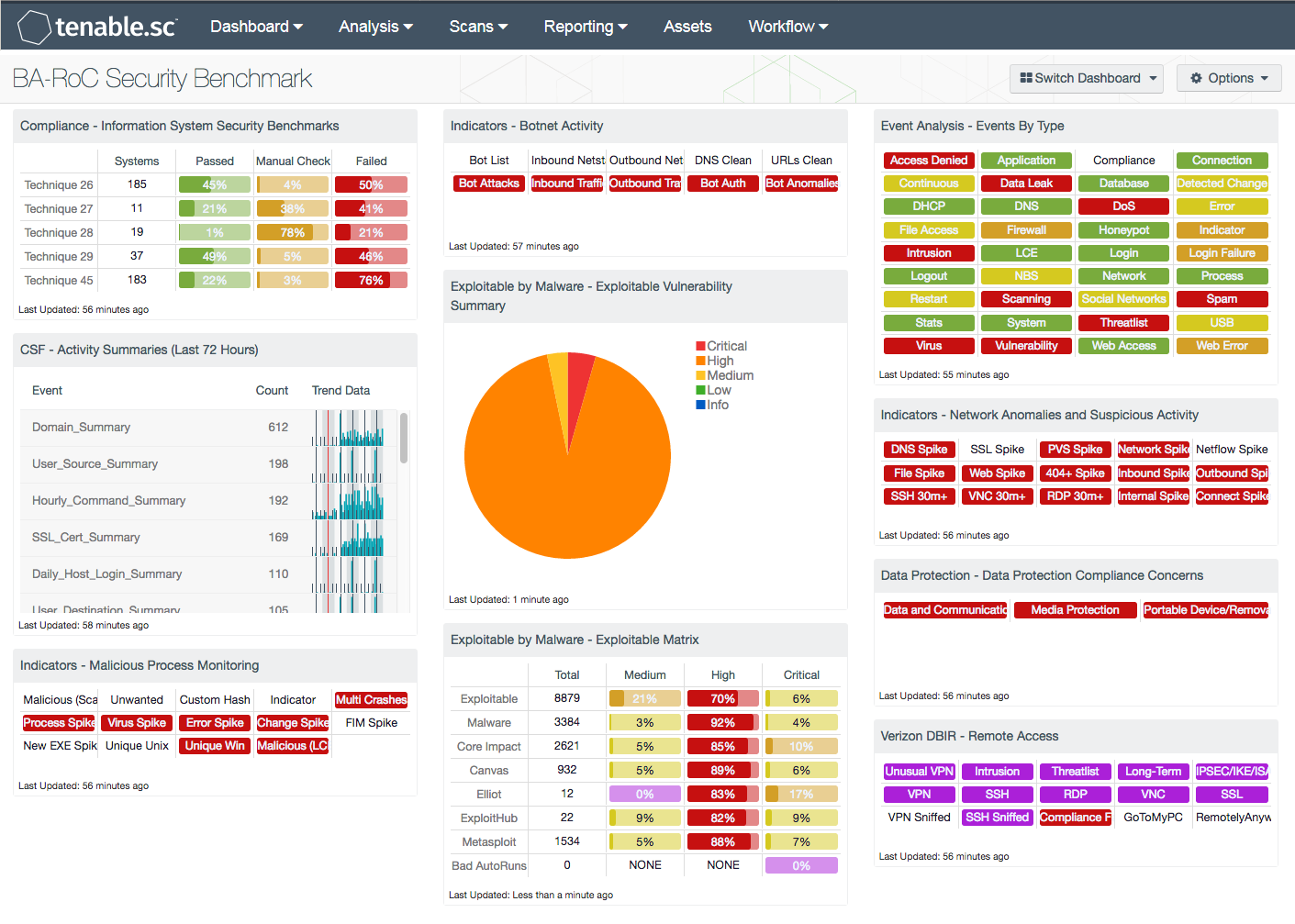
Compliance - Taiwan Bankers Association Benchmarks: This component leverages results from compliance scans to measure the system configuration compliance status of Techniques 26, 27, 28, 29, and 45 mentioned in the “Information System Security Benchmark and Usage” document.
CSF - Activity Summaries (Last 72 Hours): This component gives an overview of network access summaries for the last 72 hours and helps analysts monitor access control, as mentioned in Technique 18, "Strengthen monitoring on system loading". The component provides summaries of the previous three days, including user source, destination, and host discovered. Any spikes of events may indicate an increase in system load, while sudden absence of events may indicate system outage.
Indicators - Malicious Process Monitoring: This component takes many of the various detection technologies for botnets, malicious file hashes, anomalous network traffic, spikes in system logs, and continuous scanning activity and places them into one spot. Tenable.sc CV detects running malware, indications of compromise, and suspicious system events, such as multiple system crashes in a short time. The malware detection capability can help organizations to ensure that existing malware protection is effective. This component helps analysts monitor virus and malware protection, as covered in Techniques 49, 50, and 51, including “Establish policies to defend computer from virus or malware”, “Deploy mechanism to detect computer virus or malware”, and “Establish policies to respond on device infection”.
Indicators - Botnet Activity: This component takes many of the various detection technologies for botnets, malicious file hashes, anomalous network traffic, spikes in system logs, and continuous scanning activity and places them into one spot for botnet traffic monitoring. Tenable.sc CV detects botnet connections by checking netstat connection tables, monitoring traffic on the wire, and comparing logs from network equipment. Organizations are also able to import a customized blacklist IP database. This component helps analysts monitor virus and malware protection, as covered in Techniques 50 and 51 mentioned in the document, including “Deploy mechanism to detect computer virus or malware” and “Establish policies to respond on device infection”.
Exploitable by Malware - Exploitable Vulnerability Summary: This component displays a summary of vulnerabilities that are exploitable by malware. Tenable.sc CV detects malware by checking files against a MD5 hash database of known malware. The signature database Tenable.sc uses has signatures from more than 25 anti-virus vendors. This also helps to ensure that anti-virus software is running properly. This component gives analysts an overview of current security against viruses and malware, which is covered in Technique 49 mentioned in the document, “Establish policies to defend computer from virus or malware”.
Exploitable by Malware - Exploitable Matrix: This component is an indicator matrix of exploitable vulnerabilities. The columns show the total exploitable vulnerabilities, with columns for each severity level. The rows are organized by exploit framework, including the tag "Exploitable by Malware". Analysts are able to use the data in this component to understand the threat to the environment by known exploitation frameworks. This component helps analysts to decide which vulnerabilities to patch first, in order to best protect against the virus and malware threat covered in Technique 49 mentioned in the document, “Establish policies to defend computer from virus or malware”.
Event Analysis - Events By Type: This matrix provides a series of indicators for each event type, and is refreshed every 24 hours. This matrix allows the security administrator to receive information on current events. The color of the indicator reflects the severity: low is green, medium is yellow, high is orange, and critical is red. The different colors of the indicators signify the threat level of the event type. If no events are present, then the indicator is white. Events that are a normal event, but are more likely to have caution warranted, are green. For example, a "Detected Change" event can be a routine firewall change, or a prefetch file change on a Windows computer, both of which may not be an issue. The green indicator shows that these events need to be monitored, but might be legitimate. The medium level, which is colored yellow, indicates some sort of a problem that should be investigated. For example, "Web Error" may indicate a misconfigured server. The orange indicators are for a higher risk and should be addressed immediately. For example, as shown in the sample image, there is a "Virus" event. These events should be investigated as soon as possible. Finally, the red color indicates a critical event and provides an indication of compromise or more serious event and should be investigated over all others. This component identifies various security events, and by filtering this dashboard for critical assets only, this component can help analysts identify unexpected events in business critical applications, such as for Technique 42-1 mentioned in the document, "Prevent illegal usage of email and browsing web pages".
Indicators - Network Anomalies and Suspicious Activity: This component takes many of the various detection technologies for botnets, malicious file hashes, anomalous network traffic, spikes in system logs, and continuous scanning activity and places them into one spot. Tenable.sc CV provides an out-of-the box statistical engine to create a baseline of network traffic, and monitor traffic spikes and long-term connections. Understanding the traffic patterns helps to uncover unusual activity which may be the result of a virus or malware that was not detected by anti-virus software. This dashboard component helps analysts find suspicious activity to make sure systems are operating correctly, which is covered in Technique 50, “Deploy mechanism to detect computer virus or malware”
Data Protection - Data Protection Compliance Concerns: This component presents indicators that highlight compliance concerns associated with data, communication, and media protection. Red indicators are triggered when one or more compliance concerns have failed the compliance check or are out of the compliance range. Clicking on the indicator will bring up the vulnerability analysis screen to display details on the compliance concerns. Compliance issues highlighted within this component may indicate services that need to be disabled, permission changes, and other system hardening controls. The data should be reviewed by security teams to determine the level of risk to the organization. This component maps to Technique 31 in the document, "File access control". Customers can develop audit files and use custom compliance scans as required to do further monitoring.